Update: If you looking for a post on CA signed certificates for vCloud Director 10, go here.
Is this part of the series we will be creating CA signed certificates for vCloud Director. vCD requires two certificates, one for the HTTP service and one for the console proxy service. vCD has some specific requirements and one of them is to use Java version 7 runtime environment to produce the keys, certificates and certificate signing requests. We will still be using the Microsoft Certificate authority to sign the CSRs. See Part 1 for details on setting that up. vCD has the required tools already installed so we will be doing the main grunt work by SSHing to vCD.
There are a few things to note before we begin. This process works either during a deployment of vCD or after you have already deployed vCD. In the latter case, you will need to call the configure script for vCD in unattended mode in order to redefine the certificate store. I will go through how to do that too. You must also be sure to name the aliases in the certificate store exactly as I have them. There is no way to define the aliases in the configure script and the values I have used are the ones the script looks for when reading the certificate store. Lastly, I am using two IPs for my vCD. You can do it with one but 2 simplifies things and allows you to use port 443 for both services.
So without further ado, lets build some certificates.
Step 1. First we are going to produce two unsigned certificates and place the, in a new certificate store. (They will be replaced with signed certs later but we need the keys for the signing) Open a SSH session to your vCD instance and change to the /tmp directory. Execute the two scripts below to create the two certificates. They are placed in a certificate store called certificates.ks. You can ignore the warning about the JCEKS keystore using a propriety format. You should then have a file called certificates.ks in the /tmp directory.
/opt/vmware/vcloud-director/jre/bin/keytool -keystore certificates.ks \
-alias http \
-storepass ChangeMe \
-keypass ChangeMe \
-storetype JCEKS \
-genkeypair \
-keyalg RSA \
-keysize 2048 \
-validity 3650 \
-dname “CN=vcd-dc1-001.local, OU=Sales, O=VMware, L=Pittsford, S=New York, C=US” \
-ext “san=dns:vcd-dc1-001.local,dns:vcd-dc1-001,ip:192.168.20.81”
/opt/vmware/vcloud-director/jre/bin/keytool -keystore certificates.ks \
-alias consoleproxy \
-storepass ChangeMe \
-keypass ChangeMe \
-storetype JCEKS \
-genkeypair \
-keyalg RSA \
-keysize 2048 \
-validity 3650 \
-dname “CN=vcdconsole-dc1-001.local, OU=Sales, O=VMware, L=Pittsford, S=New York, C=US” \
-ext “san=dns:vcdconsole-dc1-001.local,dns:vcdconsole-dc1-001,ip:192.168.22.81”
Step 2. Next we going to produce a certificate signing request (CSR) that we will send on to our Certificate Authority (CA). Once you execute the two scripts below you should end up with two new files called vcd-dc1-001.csr and vcdconsole-dc1-001.csr.
/opt/vmware/vcloud-director/jre/bin/keytool -keystore certificates.ks \
-storetype JCEKS \
-storepass ChangeMe \
-certreq \
-alias http \
-file vcd-dc1-001.csr \
-ext “san=dns:vcd-dc1-001.local,dns:vcd-dc1-001,ip:192.168.20.81”
/opt/vmware/vcloud-director/jre/bin/keytool -keystore certificates.ks \
-storetype JCEKS \
-storepass ChangeMe \
-certreq \
-alias consoleproxy \
-file vcdconsole-dc1-001.csr \
-ext “san=dns:vcdconsole-dc1-001.local,dns:vcdconsole-dc1-001,ip:192.168.22.81”
Step 3. From here we need to get the CSRs signed by our lab CA. See Part 2 of this series to find out how. The output of that process will be two .cer files that contain the signed certificates. Make sure you also get a copy of the CA’s root certificate as you will need it in Step 4. See Part 1 of this series to get the CA Root certificate if you don’t already have it.
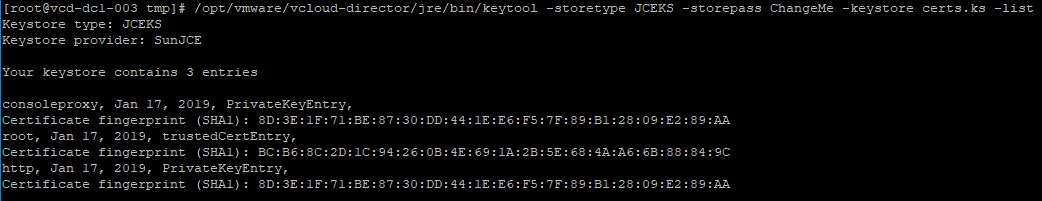
Step 4. We are now going to take the three .cer files collected in step 3 and load them into the certificate store file certificates.ks. You will need to use a tool like WinSCP to transfer the files to your vCD server. Once you have them there, execute the next three scripts to get the files into the store. Again, note that you must use the same alias names as in the script.
/opt/vmware/vcloud-director/jre/bin/keytool -keystore certificates.ks \
-storetype JCEKS \
-storepass ChangeMe \
-import \
-alias root \
-file LabCA.cer
/opt/vmware/vcloud-director/jre/bin/keytool -keystore certificates.ks \
-storetype JCEKS \
-storepass ChangeMe \
-import \
-alias http \
-file vcd-dc1-001.cer
/opt/vmware/vcloud-director/jre/bin/keytool -keystore certificates.ks \
-storetype JCEKS \
-storepass ChangeMe \
-import \
-alias consoleproxy \
-file vcdconsole-dc1-001.cer
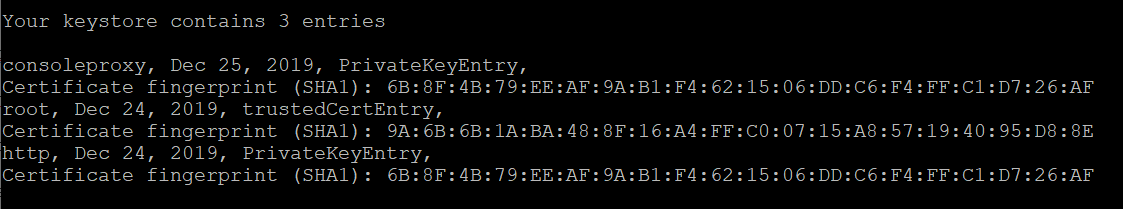
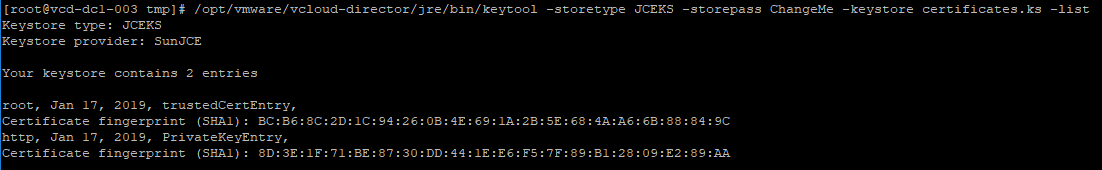
Once this is done, list the contents of the certificate store to make sure all the bits are in there.
/opt/vmware/vcloud-director/jre/bin/keytool -storetype JCEKS -storepass ChangeMe -keystore certificates.ks -list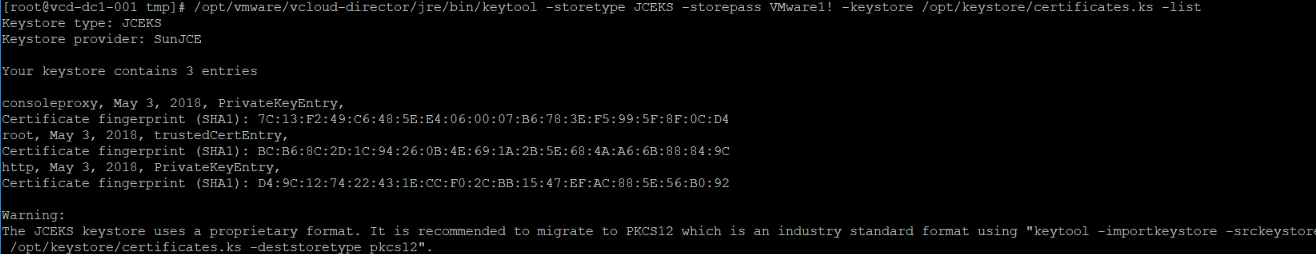
I suggest moving this file to a more permanent location. I put mine in /opt/keystore.
Step 5. We are now ready to reconfigure (in my case) vCD. In order to get the new certificate store into vCD, we need to run the configure script in unattended mode. The script I use is as follows but you may need to change it depending on your lab setup. I have installed Postgres on my vCD server so you may have to adjust if you using Oracle or MSSQL. (If you are, you should consider switching to Postgres and support for Oracle is already depreciated in 9.1 and MSSQL will be depreciated in the next release! This is good news as VMware moves to making vCD available as an appliance.)
Stop vCD:
service vmware-vcd stop
Update the configuration:
/opt/vmware/vcloud-director/bin/configure \
-ip 192.168.20.81 –primary-port-https 443 \
-cons 192.168.22.81 –console-proxy-port-https 443 \
-dbtype postgres -dbhost vcd-dc1-001.local -dbname vcloud -dbuser vcloud -dbpassword vcloudpass \
-k /opt/keystore/certificates.ks -w ChangeMe \
-loghost vrli-dc1.local \
–enable-ceip true \
-unattended
Start vCD:
service vmware-vcd start
And that’s it. Give vCD a minute or two to get going and then open a new browser session to your instance. It should be nice and secure now.